A) Misconfigured firewall
B) Clear text credentials
C) Implicit deny
D) Default configuration
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A systems administrator has created network file shares for each department with associated security groups for each role within the organization. Which of the following security concepts is the systems administrator implementing?
A) Separation of duties
B) Permission auditing
C) Least privilege
D) Standard naming conversation
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The Chief Information Officer (CIO) has determined the company's new PKI will not use OCSP. The purpose of OCSP still needs to be addressed. Which of the following should be implemented?
A) Build an online intermediate CA.
B) Implement a key escrow.
C) Implement stapling.
D) Install a CRL.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An in-house penetration tester is using a packet capture device to listen in on network communications. This is an example of:
A) Passive reconnaissance
B) Persistence
C) Escalation of privileges
D) Exploiting the switch
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Datacenter employees have been battling alarms in a datacenter that has been experiencing hotter than normal temperatures. The server racks are designed so all 48 rack units are in use, and servers are installed in any manner in which the technician can get them installed. Which of the following practices would BEST alleviate the heat issues and keep costs low?
A) Utilize exhaust fans.
B) Use hot and cold aisles.
C) Airgap the racks.
D) Use a secondary AC unit.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Moving laterally within a network once an initial exploit is used to gain persistent access for the purpose of establishing further control of a system is known as:
A) pivoting.
B) persistence.
C) active reconnaissance.
D) a backdoor.
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following BEST explains how the use of configuration templates reduces organization risk?
A) It ensures consistency of configuration for initial system implementation.
B) It enables system rollback to a last known-good state if patches break functionality.
C) It facilitates fault tolerance since applications can be migrated across templates.
D) It improves vulnerability scanning efficiency across multiple systems.
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following are considered to be "something you do"? (Choose two.)
A) Iris scan
B) Handwriting
C) CAC card
D) Gait
E) PIN
F) Fingerprint
H) D) and F)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An audit has revealed that database administrators are also responsible for auditing database changes and backup logs. Which of the following access control methodologies would BEST mitigate this concern?
A) Time of day restrictions
B) Principle of least privilege
C) Role-based access control
D) Separation of duties
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security administrator in a bank is required to enforce an access control policy so no single individual is allowed to both initiate and approve financial transactions. Which of the following BEST represents the impact the administrator is deterring?
A) Principle of least privilege
B) External intruder
C) Conflict of interest
D) Fraud
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security architect has convened a meeting to discuss an organization's key management policy. The organization has a reliable internal key management system, and some argue that it would be best to manage the cryptographic keys internally as opposed to using a solution from a third party. The company should use:
A) the current internal key management system.
B) a third-party key management system that will reduce operating costs.
C) risk benefits analysis results to make a determination.
D) a software solution including secure key escrow capabilities.
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The Chief Technology Officer (CTO) of a company, Ann, is putting together a hardware budget for the next 10 years. She is asking for the average lifespan of each hardware device so that she is able to calculate when she will have to replace each device. Which of the following categories BEST describes what she is looking for?
A) ALE
B) MTTR
C) MTBF
D) MTTF
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An information security specialist is reviewing the following output from a Linux server. 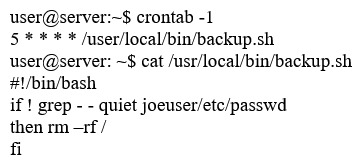 Based on the above information, which of the following types of malware was installed on the server? /local/
Based on the above information, which of the following types of malware was installed on the server? /local/
A) Logic bomb
B) Trojan
C) Backdoor
D) Ransomware
E) Rootkit
G) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
After reports of slow internet connectivity, a technician reviews the following logs from a server's host-based firewall: 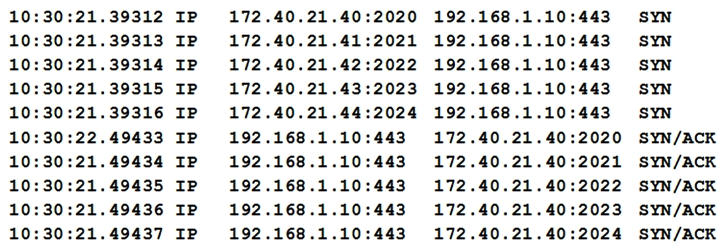 Which of the following can the technician conclude after reviewing the above logs?
Which of the following can the technician conclude after reviewing the above logs?
A) The server is under a DDoS attack from multiple geographic locations.
B) The server is compromised, and is attacking multiple hosts on the Internet.
C) The server is under an IP spoofing resource exhaustion attack.
D) The server is unable to complete the TCP three-way handshake and send the last ACK.
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security analyst is reviewing an assessment report that includes software versions, running services, supported encryption algorithms, and permission settings. Which of the following produced the report?
A) Vulnerability scanner
B) Protocol analyzer
C) Network mapper
D) Web inspector
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security, who is analyzing the security of the company's web server, receives the following output: 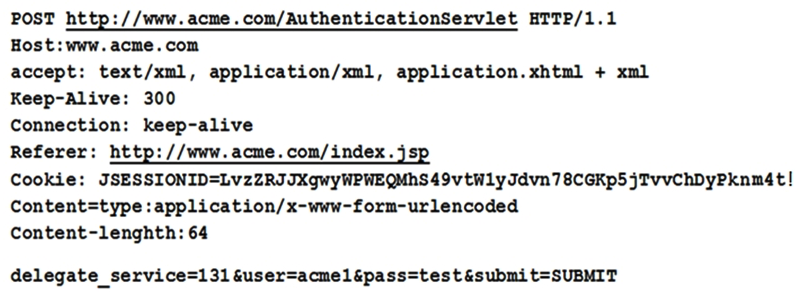 Which of the following is the issue?
Which of the following is the issue?
A) Code signing
B) Stored procedures
C) Access violations
D) Unencrypted credentials
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following command line tools would be BEST to identify the services running in a server?
A) Traceroute
B) Nslookup
C) Ipconfig
D) Netstat
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security analyst wishes to scan the network to view potentially vulnerable systems the way an attacker would. Which of the following would BEST enable the analyst to complete the objective?
A) Perform a non-credentialed scan.
B) Conduct an intrusive scan.
C) Attempt escalation of privilege.
D) Execute a credentialed scan.
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security analyst is investigating a security breach. Upon inspection of the audit an access logs, the analyst notices the host was accessed and the /etc/passwd file was modified with a new entry for username "gotcha" and user ID of 0. Which of the following are the MOST likely attack vector and tool the analyst should use to determine if the attack is still ongoing? (Select TWO)
A) Logic bomb
B) Backdoor
C) Keylogger
D) Netstat
E) Tracert
F) Ping
H) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Fuzzing is used to reveal which of the following vulnerabilities in web applications?
A) Weak cipher suites
B) Improper input handling
C) DLL injection
D) Certificate signing flaws
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Showing 1081 - 1100 of 1164
Related Exams